Cloud Trust Starts With Identity Control
HYMDL CIEM/NHI delivers centralized identity governance, access control, and automation for both human and non-human identities. It empowers organizations with full visibility into entitlements, policy enforcement, and continuous least-privilege assurance.
CIEM/NHI Advantages
Continuously discover and monitor human and machine identities, their access levels, and permissions across AWS, Azure, and GCP.
Uncover overprivileged accounts and identify access anomalies using graph-based identity analytics.
Automatically detect and enforce least privilege policies to reduce lateral movement and insider risk.
Integrate with cloud-native tools to manage and automate secrets rotation, policy enforcement, and compliance tracking.
Introducing HYMDL CIEM/NHI
Comprehensive Identity Intelligence for Cloud Security
Unified Identity Inventory
HYMDL CIEM/NHI visualizes all human and non-human identities with their roles, policies, and activity in one dynamic interface.
Least-Privilege Enforcement
Secrets Management & Rotation
Role Visualizations & Risk Scores
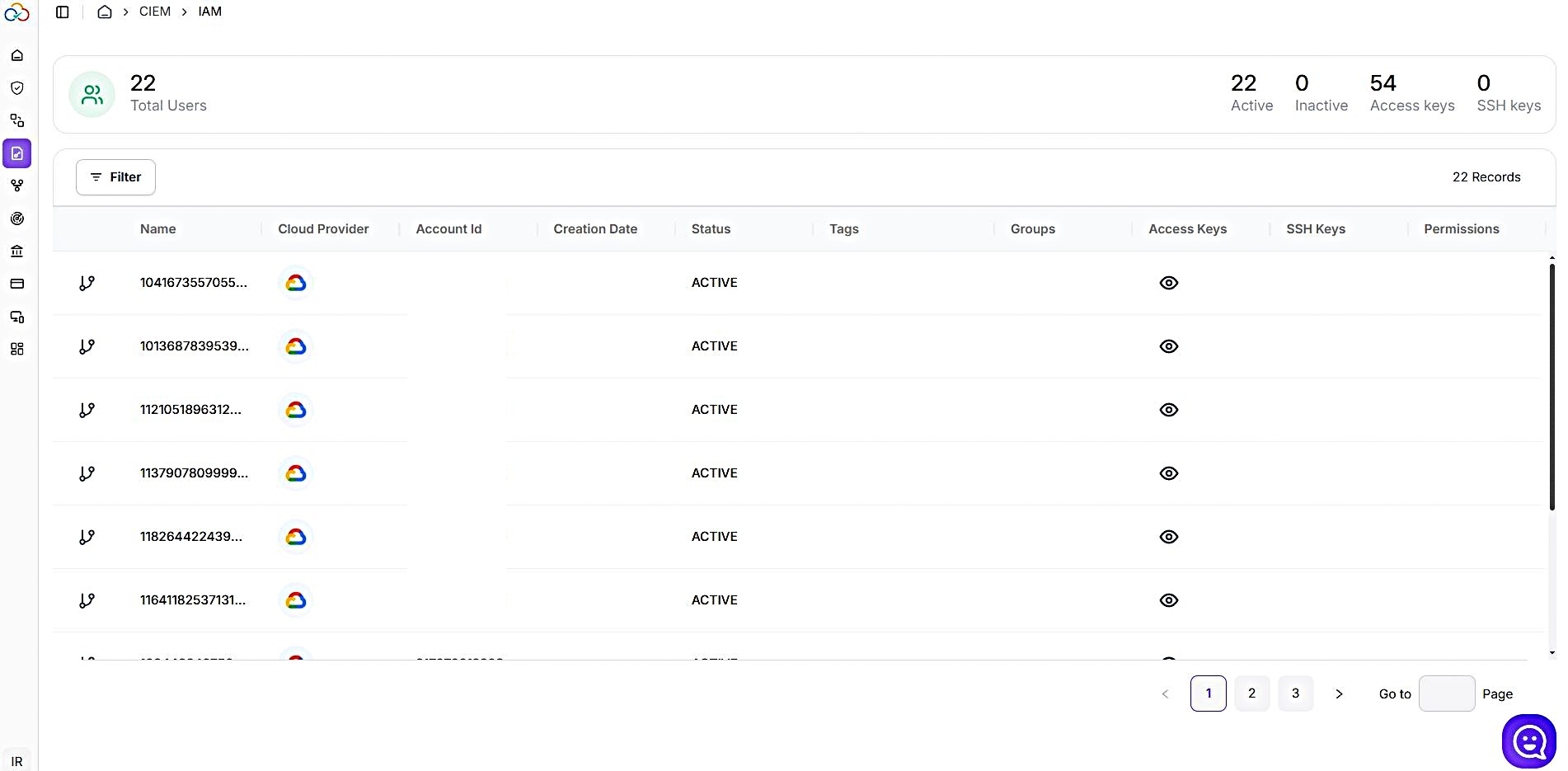
HYMDL - Discover More
HYMDL CIEM/NHI is a cloud identity and entitlement management solution for managing human and non-human identities. It centralizes access governance and automates least-privilege enforcement.
CIEM analyzes access rights and entitlements across all cloud accounts, identifying over-privileged identities and enforcing least privilege policies.
HYMDL’s NHI module inventories service accounts, keys, and tokens, applying security policies to enforce lifecycle management, visibility, and secrets rotation.
Yes. HYMDL CIEM/NHI supports identity visibility and access control across AWS, Azure, GCP, and hybrid cloud environments.
Security teams, cloud architects, IAM specialists, and DevSecOps practitioners benefit from full access visibility and policy automation.
HYMDL CIEM/NHI is agentless and integrates with cloud-native APIs for identity discovery, analytics, and continuous enforcement.

Integrations
Hymdl integrates with your cloud providers and existing tools to build a rich ecosystem of data and insights.

AWS
Crawl all AWS Accounts

Azure
Crawl all Azure Subscriptions

GCP
Crawl all GCP Projects

Jira
Create Jira tickets for findings

Slack
Notify in Slack

Teams
Notify in Teams

ServiceNow
ITIL Integration
